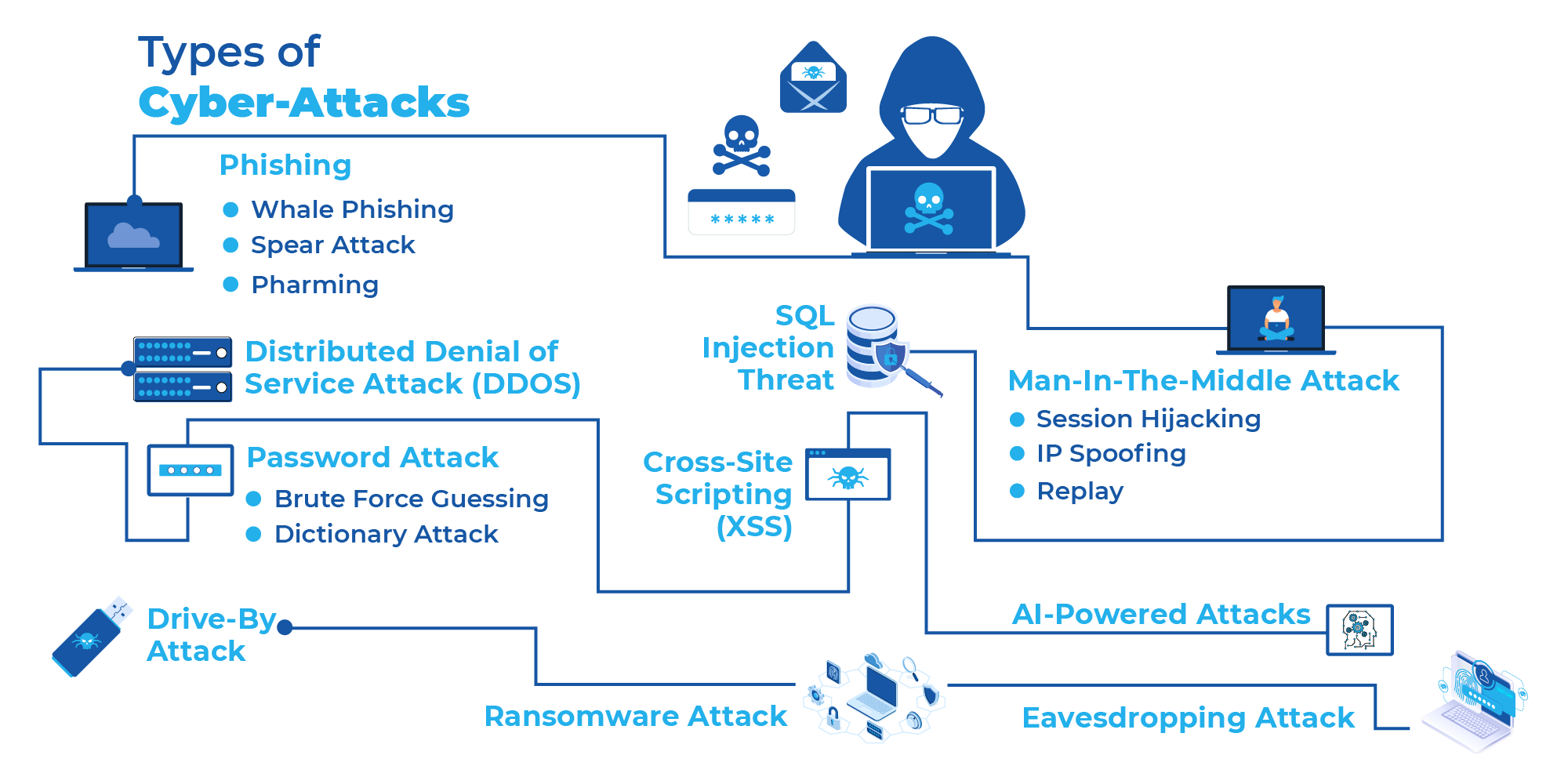
Cybersecurity Ventures opines that global cybercrime will cost the world a whopping $10.5 trillion annually by 2025.
Every day headlines bring new reminders that the future is uncertain. On top of it, cybercrime is becoming more aggressive and dangerous for enterprises worldwide. Thanks to the ever-evolving digital age and the massive volumes of data, cybercriminals are executing intricate attacks at lightning speed now more than ever.
The abundance of cyber risks demonstrates the need for advanced cybersecurity in organizations. Despite that, most organizations still depend on traditional cybersecurity practices – such as proxy firewalls, IPS, anti-virus software, spam filters, etc.
The bitter truth is, while these practices were effective in the past, the advancement in technology has made cyber threats immune to them. This brings up a crucial question – how will the next wave of cybersecurity innovation combat crippling cyberattacks?
This blog answers it while covering the emerging threats faced by businesses. Then, we’ll talk about the newer, smarter approaches for risk-informed cybersecurity investments.
Emerging Cyber Threats Faced by Enterprises
5 Ways of Curbing Cybercrime Using Cognitive Technology
Fact: As per IBM’s Cost of a Data Breach Report 2020, organizations took 207 days to identify and 73 days to contain a security breach.
Traditional cybersecurity systems are centered around protecting structured data, i.e., the data in a pre-defined format; accounts for 20% or less of enterprise data. This renders the remaining (unstructured) data unprotected. If that data is monitored and secured, it can prove to be a game-changer for detecting cyber threats proactively.
Enter cognitive technology; its building blocks, like ML, NLP, and deep analytics, analyze complex data and glean insights for accurate threat detection. This allows enterprises to mitigate the risks coming their way.
Not convinced yet, huh? Challenge accepted. Here’s how cognitive technology is remodeling the realms of cybersecurity and why you should bet on it.
1. Leveraging NLP for Monitoring Malicious Intent and Threat Hunting
A Verizon report found that nearly 80% of attackers compromised their targets within days, while only about a third of companies detected the attacks during the same time frame.
Cyber threat hunting is the need of the hour for enterprises as it digs deeper to find the malicious activities that might have slipped past the initial defenses. Traditional methods like tactics, techniques, and procedures (TTP) hunting tend to struggle while detecting advanced or complex threats.
Fueled by NLP, cognitive technology automates threat hunting procedures and identifies users with malicious intent well in advance. NLP combs through massive volumes of data at lightning speed to zero-in on any intrusion attempts by attackers. It segregates legitimate and malicious emails or domains using Autonomous Systems Number (ASN) mapping.
Hackers use spoofing techniques that impersonate any legitimate website or company. But thanks to ASN mapping, NLP identifies malicious domains hosted on an IP network from that of the legitimate domain. For instance, if 23456 and 87654 are ASNs assigned to a website, the ASNs of the impersonated domain used for cybercrime will be identified and reported by cognitive technology.
2. Modeling Behavior for Vulnerability Management
According to a study, a whopping 18,000+ new vulnerabilities were reported in 2020, out of which 10,000 were critical or high severity – an all-time high.
Enterprises have countless vulnerability points across information systems or processes that hackers can target. That’s why vulnerability management has become an indispensable part of organizations today. While traditional VM practices wait for cybercriminals to cause high-risk vulnerabilities to take necessary actions, cognitive technology empowers you to be more proactive.
Cognitive technology leverages ML techniques like User and Event Behavioral Analytics (UEBA) that automatically detect and highlight the unusual behavior of users on corporate networks, routers, applications, servers, and endpoints.
It categorizes, rates the potential attacks, and signals any type of vulnerable points, including zero-day unknown attacks and insider threats. Rather than being dependent on human intervention, it simply finds the immediate solution to stop the threat, such as blocking it.
3. Put Incident Response Management in Place
As per a study by IBM, 77% of companies don’t have a cybersecurity incident response plan applied across the enterprise.
Incident Response Management is an organized and documented strategy to address and manage security incidents, breaches, and cyberattacks. Shockingly, the majority of organizations lack incident response plans. This makes inroads for attackers smooth.
As Ted Julian from IBM says, “Failing to plan is a plan to fail when it comes to responding to a cybersecurity incident.”
Embedding cognitive technology can fix that. Its intelligent reporting helps the organization to easily access all log and event data – such as routers, firewalls, and intrusion prevention systems – in one dashboard. This enables security analysts with improved context to detect breaches, better respond to security alerts, remediate vulnerabilities, and much more.
4. Secure Data in-Transit & At-Rest
The average large enterprise generates more than 12,000 security events per second, nearly a billion events every day, according to FireEye data.
Moving data from one destination to another, such as across the internet or through a private network, can invite a horde of Man-in-the-Middle (MITM) attacks. This can hurt the integrity and security of your data. Attackers can jeopardize the data, whether it is in transit or at rest. Fret not, cognitive technology comes to the rescue here too.
Using the strongest encryption standard, i.e. AES-256 encryption, cognitive platforms like SearchUnify leverage multi-factor authentication for protecting the data at rest. Moreover, it uses TLS 1.3 encryption to safeguard data once it reaches the destination and lays at rest.
Such encryptions are deemed uncrackable and can protect any sensitive data. For instance, AES-256 encryption is also known as a “military-graded” cipher because it requires a 256-bit key. If a hacker tries to break into the security, he will have to try 2256 different combinations to ensure the right one is included, the odds of which are slim to none.
5. Battling Bots
Cybercriminals are leaving no stone unturned to develop new intrusion techniques. The latest ones include the misuse and abuse of AI and ML to manipulate legitimate content, password hacking, and human impersonation on social media. Traditional security systems cannot even identify such threats, let alone fight them. Moreover, enterprises cannot combat automated threats with manual responses.
Irony – cognitive tech against cognitive tech.
It can be both a sword and a shield to combat malicious threats, breaches, and cyber risks. In simple words, cognitive technology can differentiate between a good bot and a bad bot. It can be taught to identify patterns, flag server discrepancies, detect risk zones & vulnerabilities, and flag any anomalies for the security analysts.
Transcend Your Cybersecurity Boundaries With Cognitive Technology!
In the era of cyberattacks, conformity with the latest data security & privacy management standards is mandatory for every enterprise. SearchUnify has always been proactive and stern when it comes to information security and privacy protection. So much so that it is GDPR-compliant and has obtained several authoritative certifications including HIPAA, SSAE 18 SOC 1, SOC 2 Type II, SOC 3, GDPR, ISO 27001, and ISO/IEC 27001:2019.
If you want to strengthen your data security with cognitive technology, reach out to us. Request a free demo today!